Certificate Basics
Basics about Certificate
CA
A certificate authority or certification authority (CA) is an entity that issues digital certificates. A digital certificate certifies the ownership of a public key by the named subject of the certificate. This allows others (relying parties) to rely upon signatures or on assertions made about the private key that corresponds to the certified public key. A CA acts as a trusted third party—trusted both by the subject (owner) of the certificate and by the party relying upon the certificate. The format of these certificates is specified by the X.509 standard.
Top providers are VeriSign, Digicert, GeoTrust, Comodo, GoDaddy…
Digital Certificate
a public key certificate, also known as a digital certificate or identity certificate, is an electronic document used to prove the ownership of a public key. The certificate includes information about the key, information about the identity of its owner (called the subject), and the digital signature of an entity that has verified the certificate’s contents
X.509 is a standard defining the format of public key certificates. X.509 certificates are used in many Internet protocols, including TLS/SSL, which is the basis for HTTPS[1], the secure protocol for browsing the web.
There are usually 3 types of certificates
- root certificate is a self-signed certificate used to sign other certificates. Also sometimes called a trust anchor.
- Intermediate certificate is a certificate used to sign other certificates. An intermediate certificate must be signed by another intermediate certificate, or a root certificate.
- End-entity or leaf certificate is any certificate that cannot be used to sign other certificates. For instance, TLS/SSL server and client certificates, email certificates, code signing certificates, and qualified certificates are all end-entity certificates.
Certificate from root certificate to end-entity certificate forms a chain call certificate chain.
You can view a certificate for a website from Chrome title bar. Here is an example for google.com
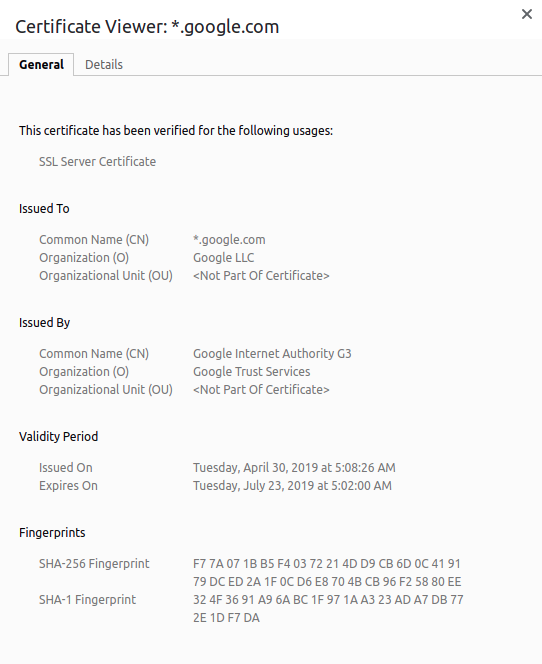
Structure
- Certificate
- Version Number
- Serial Number
- Signature Algorithm ID
- Issuer Name
- Validity period
- Not Before
- Not After
- Subject name
- Subject Public Key Info
- Public Key Algorithm
- Subject Public Key
- Issuer Unique Identifier (optional)
- Subject Unique Identifier (optional)
- Extensions (optional)
- …
- Certificate Signature Algorithm
- Certificate Signature
For sample X.509 certificate see [certificate example from Wikipedia](Sample X.509 certificates)
Certificate Fingerprint
Certificate Fingerprint is the hash of the whole certificate in der format.
Fingerprint example
1 | MD5: 1B:DE:A8:E3:11:86:FD:89:8C:C1:D3:80:EE:19:D3:A8 |
Common Extensions
There are several commonly used filename extensions for certificates.
- .pem – (Privacy-enhanced Electronic Mail) Base64 encoded DER certificate, enclosed between “—–BEGIN CERTIFICATE—–” and “—–END CERTIFICATE—–”
- .cer, .crt, .der – usually in binary DER form, but Base64-encoded certificates are common too
- .p7b, .p7c – PKCS#7 SignedData structure without data, just certificate(s) or CRL(s)
- .p12 – PKCS#12, may contain certificate(s) (public) and private keys (password protected). PKCS #12 is the successor to Microsoft’s “PFX”
- .pfx – PFX, predecessor of PKCS#12 (usually contains data in PKCS#12 format, e.g., with PFX files generated in IIS)
Self-signed vs CA signed certificates
Both self-signed and CA signed certificates provide encryption for data in motion. A CA-signed certificate also provides authentication - a level of assurance that the site is what it reports to be, and not an impostor website.
Browser will give warnings for certificate not issued by a CA.
Certificate Signing Request
csr extension is for certificate signing request file. It is a request sent from an applicant to certificate authority in order to apply for a digital identity certificate. CA creates SSL Certifiate using CSR. see wikipedia for CSR.
Components of CSR are
- Common Name
- Organization
- Organization Unit
- City/Locality
- State/County/Region
- Country
- Email address
- Public Key
Reference